Table of Contents
In this article, I will take you through the steps to password protect GRUB Boot Loader in Ubuntu 20.04 LTS but before that let me ask you a quick question - Do you know which is the default boot loader on most of the Linux Systems if not all ? Well, you might have guessed it right. It is none other than GRUB bootloader. GRUB is also known as multiboot boot loader as it can not only boot Linux OS but also Windows OS so it can be used to boot both the operating systems. Same cannot be done by Microsoft Windows Boot Loader. Hence GRUB is always preferred over the others. More about GRUB Bootloader.
When it comes to Linux Security, there is a chance that an attacker or a person might reboot or restart the System to get into Single user mode where they can reset the root password to get the Control of your System. Hence it is always recommended to password protect your Boot Loader to avoid this kind of unwanted situations. This can be done in few simple steps as explained in the below section.
What is Boot Loader
Boot Loader also known by the name boot manager or boot strap loader is a small program which resides on EPROM, ROM or other non-volatile memory responsible for loading a large program called Operating System in the main memory.
What is GRUB
GRUB stand as Grand Unified Boot Loader. It is the default boot loader in most of the modern Linux Systems. GRUB was originally designed and implemented by Erich Stefan Boleyn.

How to Password Protect GRUB Boot Loader in Ubuntu 20.04 LTS
Also Read: How to Share Folder Between Windows 10 Host OS and Ubuntu 20.04 Guest OS
Step 1: Prerequisites
a) You should have a running Ubuntu 20.04 LTS Server.
b) You should have sudo or root access to run privileged commands.
c) You should have grub-mkpasswd-pbkdf2 and update-grub utility available in your System.
Step 2: Generate a Hashed Password
In the first step, you need to generate a Hashed Password using grub-mkpasswd-pbkdf2 command. The hashed password will start from the keyword grub.pbkdf2... as shown in the below output. You need to copy this password.
root@localhost:~# grub-mkpasswd-pbkdf2
Enter password:
Reenter password:
PBKDF2 hash of your password is grub.pbkdf2.sha512.10000.C413GH4D904408270DC6B624A2EB947B677E29D63AB2C4B8987AD166FA55729907D5B5ED59AD52CC5842D33ECBC4B77BF04CAED637364B73EF6D50A10AA963CD.220D34777C4556A5B353DFB0C960CDF25DA00AC60C429A88476AF0A69ED0868EE769A7B2A93292426564D6729DB53CB35A2E9A125B793C85969A30C304A7058F
Step 3: Setup the Password
Now all you need to do is to open the 00_header file using nano /etc/grub.d/00_header command and paste the below comments with the hashed password at the end of the file. Then save and close the file by Pressing Ctrl+X and then give Y to confirm.
NOTE:
cat << EOF
set superusers="cyberithub"
password_pbkdf2 cyberithub grub.pbkdf2.sha512.10000.C413GH4D904408270DC6B624A2EB947B677E29D63AB2C4B8987AD166FA55729907D5B5ED59AD52CC5842D33ECBC4B77BF04CAED637364B73EF6D50A10AA963CD.220D34777C4556A5B353DFB0C960CDF25DA00AC60C429A88476AF0A69ED0868EE769A7B2A93292426564D6729DB53CB35A2E9A125B793C85969A30C304A7058F
EOF
Step 4: Update the GRUB
Then update the GRUB configuration by using update-grub command. This will automatically combines the settings from the /etc/default/grub file, /etc/default/grub.d/init-select.cfg file and others one, creating a /boot/grub/grub.cfg file which will be read during the boot process.
root@localhost:~# update-grub
Sourcing file `/etc/default/grub'
Sourcing file `/etc/default/grub.d/init-select.cfg'
Generating grub configuration file ...
Found linux image: /boot/vmlinuz-5.11.0-40-generic
Found initrd image: /boot/initrd.img-5.11.0-40-generic
Found linux image: /boot/vmlinuz-5.8.0-41-generic
Found initrd image: /boot/initrd.img-5.8.0-41-generic
Found memtest86+ image: /boot/memtest86+.elf
Found memtest86+ image: /boot/memtest86+.bin
done
Step 5: Restart the System
It is now time to test the configuration by restarting the system using init 6 or reboot command.
root@localhost:~# init 6
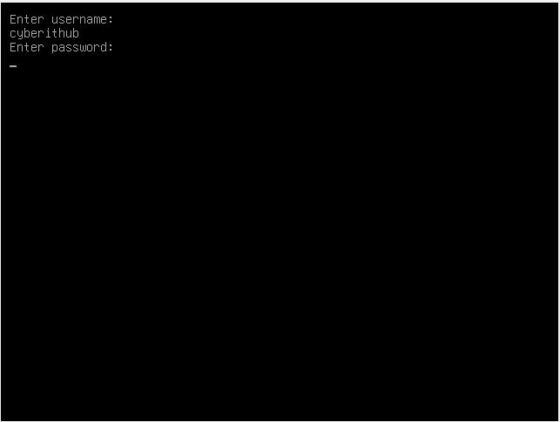
Step 6: Test the Configuration
Once the system restarts, immediately you should see a screen like below where GRUB will ask for username and password to boot the System. Here you need to provide the username and password which you had setup in Step 3. In our case username will be cyberithub. After successful authentication, you might notice that Ubuntu will boot normally hence confirming password protection of GRUB Boot Loader.

Greetings
How can I undo the grab password protection. it seems I logged out of the Ubuntu laptop because I tried to use my own username. please help me.
thank you !!